CloudFlare对于DDos拦截功能可以有效减缓网站受到的攻击,
透过5秒钟的JavaScript Challenge检查拦截不正常的访问,
但是攻击大多来自国外,
国内也使用JavaScript Challenge拦截其实不太合理,
可能会影响不少访客的浏览体验,
以前CloudFlare的IP防火墙在企业版以上的方案可以设定国家为白名单,
现在CloudFlare已经提供所有方案的用户都能使用这项功能,
直接将特定的国家配置白名单即可让站点抗DDos同时不影响国内访客的浏览体验。
CloudFlare服务官网 https://www.cloudflare.com
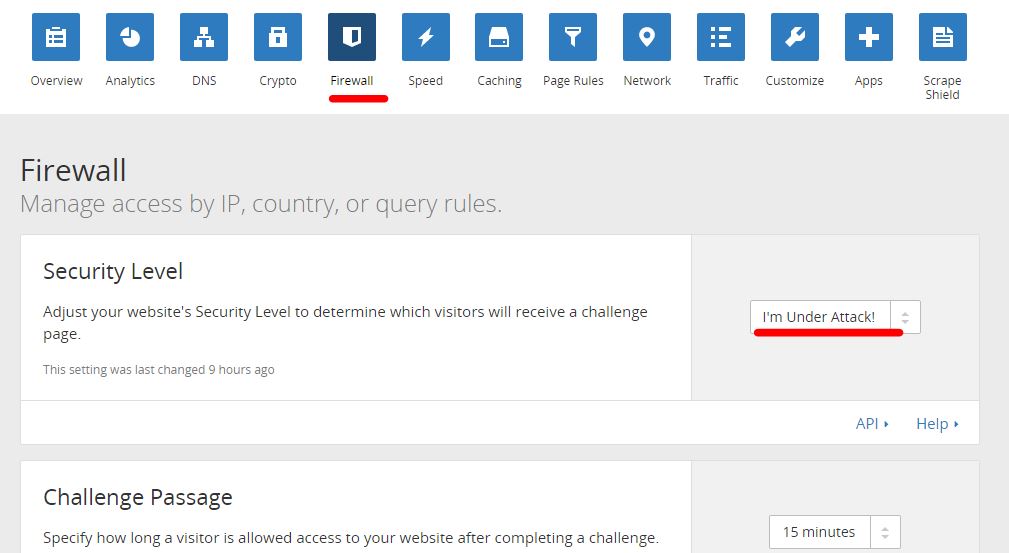
先登入CloudFlare控制面板,
开启Firewall,配置安全等级为”I’m Under Attack!”
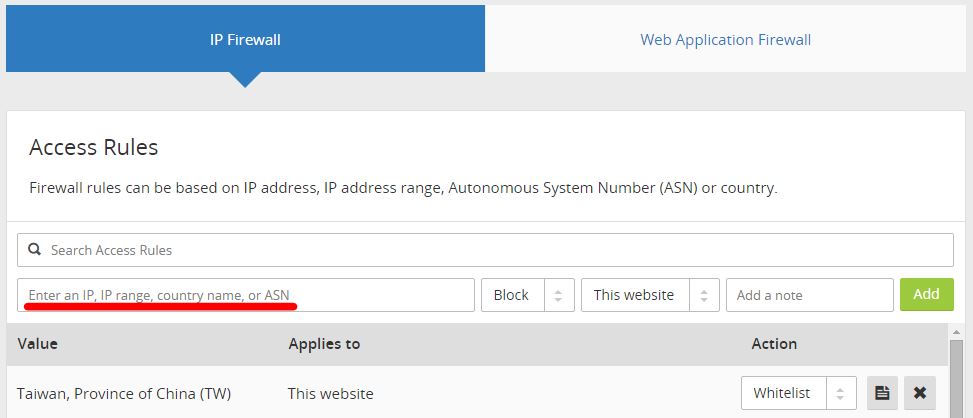
在IP Firewall可以键入IP、IP范围、Autonomous System Number (ASN)、国家代码
这里请输入您家中使用的固定IP以及您所在的国家配置为”Whitelist”
而攻击来源的国家除了可以用目前默认的JavaScript Challenge拦截,
也能配置”CAPTCHA”提高拦截的验证难度,甚至也能直接”Block”禁止访问,
即可透过CloudFlare有效拦截攻击但不影响国内访客浏览体验。
点选这里查看IP Firewall的说明(截图自CloudFlare功能注释)
对于原始主机来说,重点就是要拦截CloudFlare以外的IP访问,
CloudFlare的IP范围 https://www.cloudflare.com/ips/
如果是Apache主机可以透过htaccess新增(以IPv4示范)
order deny,allow deny from all allow from 103.21.244.0/22 allow from 103.22.200.0/22 allow from 103.31.4.0/22 allow from 104.16.0.0/12 allow from 108.162.192.0/18 allow from 131.0.72.0/22 allow from 141.101.64.0/18 allow from 162.158.0.0/15 allow from 172.64.0.0/13 allow from 173.245.48.0/20 allow from 188.114.96.0/20 allow from 190.93.240.0/20 allow from 197.234.240.0/22 allow from 198.41.128.0/17 allow from 199.27.128.0/21
如果是Nginx主机
Nginx comes with a simple module called ngx_http_access_module to allow or deny access to IP address.
location / {
# allow CloudFlare
allow 103.21.244.0/22; allow 103.22.200.0/22; allow 103.31.4.0/22; allow 104.16.0.0/12; allow 108.162.192.0/18; allow 131.0.72.0/22; allow 141.101.64.0/18; allow 162.158.0.0/15; allow 172.64.0.0/13; allow 173.245.48.0/20; allow 188.114.96.0/20; allow 190.93.240.0/20; allow 197.234.240.0/22; allow 198.41.128.0/17; allow 199.27.128.0/21; # drop rest of the world
deny all;
}
如果是VPS请在iptables键入
#CloudFlare proxies access restriction #Allow HTTP(port 80) from CloudFlare
iptables -A INPUT -s 103.21.244.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 103.22.200.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 103.31.4.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 104.16.0.0/12 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 108.162.192.0/18 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 131.0.72.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 141.101.64.0/18 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 162.158.0.0/15 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 172.64.0.0/13 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 173.245.48.0/20 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 188.114.96.0/20 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 190.93.240.0/20 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 197.234.240.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 198.41.128.0/17 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 199.27.128.0/21 -p tcp --dport http -j ACCEPT
#Block HTTP from other sources
iptables -A INPUT -p tcp --dport http -j DROP
#Allow HTTPS(port 443) from CloudFlare
iptables -A INPUT -s 103.21.244.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 103.22.200.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 103.31.4.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 104.16.0.0/12 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 108.162.192.0/18 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 131.0.72.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 141.101.64.0/18 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 162.158.0.0/15 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 172.64.0.0/13 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 173.245.48.0/20 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 188.114.96.0/20 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 190.93.240.0/20 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 197.234.240.0/22 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 198.41.128.0/17 -p tcp --dport http -j ACCEPT
iptables -A INPUT -s 199.27.128.0/21 -p tcp --dport http -j ACCEPT
#Block HTTPS from other sources
iptables -A INPUT -p tcp --dport https -j DROP
以上配置可以降低原始主机IP直接被DDos的情形,
希望对于使用CloudFlare的站长们有所帮助。